Keeping Personal Data Protected From Data Breaches

If your company stores or handles personal data, you must take reasonable steps to keep it safe from unauthorized access. If you do experience a data breach, you must notify affected individuals and any relevant authorities.
So, where do these obligations come from, and why are you forced to comply with them?
If you handle personal data, there are a few major privacy laws you should be aware of. These laws are:
- General Data Protection Regulation (GDPR) - EU
- California Consumer Privacy Act (CCPA) - California
- Stop Hacks and Improve Electronic Data Security Act (SHIELD) - New York
- Personal Information Protection and Electronic Documents Act (PIPEDA) - Canada
Their principles are similar, which means we can summarize your main obligations quite simply.
If you handle personal data, you must:
- Have a clear plan for keeping it safe
- Implement reasonable cybersecurity measures throughout your organization
- Offer employees comprehensive, frequent training on data protection and privacy laws
- Explain to customers and individuals how you plan on protecting their data
- Have clear reporting procedures for notifying affected individuals about a data breach
- Review your data security policies regularly to ensure they're still effective
What steps should you take? It can depend on:
- Your business sector (some sectors, such as healthcare, have more specific compliance requirements than others)
- Your company size
- The type and amount of personal data you handle
You only need to take steps that are reasonable and proportionate for your company. For example, a small retailer is unlikely to have the same security measures in place as a large healthcare firm, and that's okay.
We'll go over compliance strategies in more detail later, but for now, here are some examples of common steps you can take to prevent data breaches:
- Limit employee access to personal data
- Implement data encryption
- Use antivirus software
- Conduct employee training on good security practices
But what is "personal data" anyway, what constitutes a "breach" and how, specifically, can businesses reduce the risk of a breach affecting their organization?
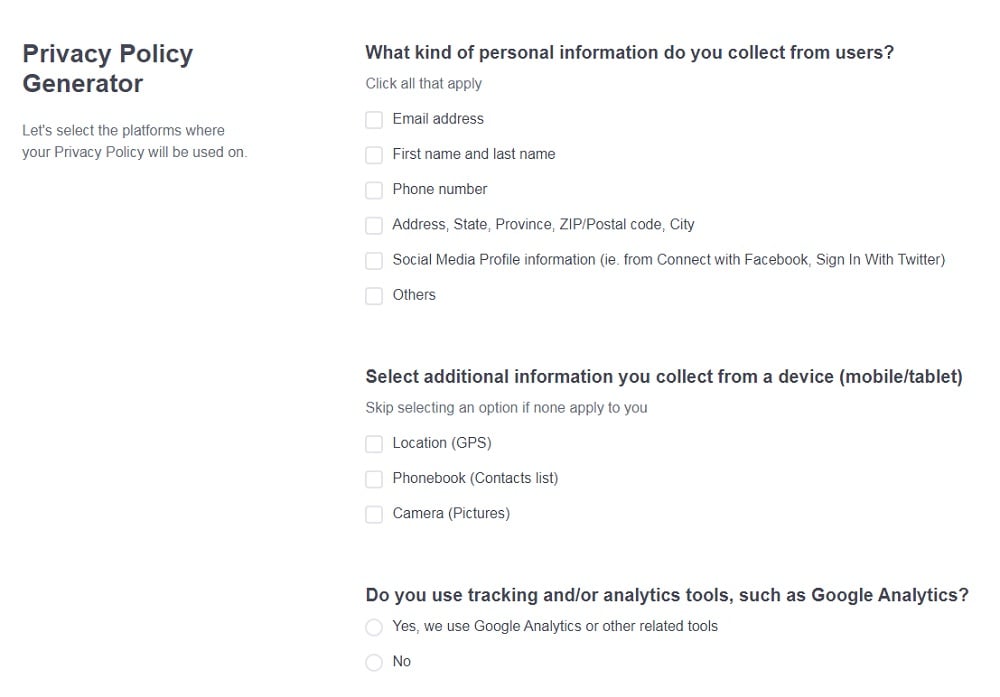
Need a Privacy Policy? Our Privacy Policy Generator will help you create a custom policy that you can use on your website and mobile app. Just follow these few easy steps:
- Click on "Start creating your Privacy Policy" on our website.
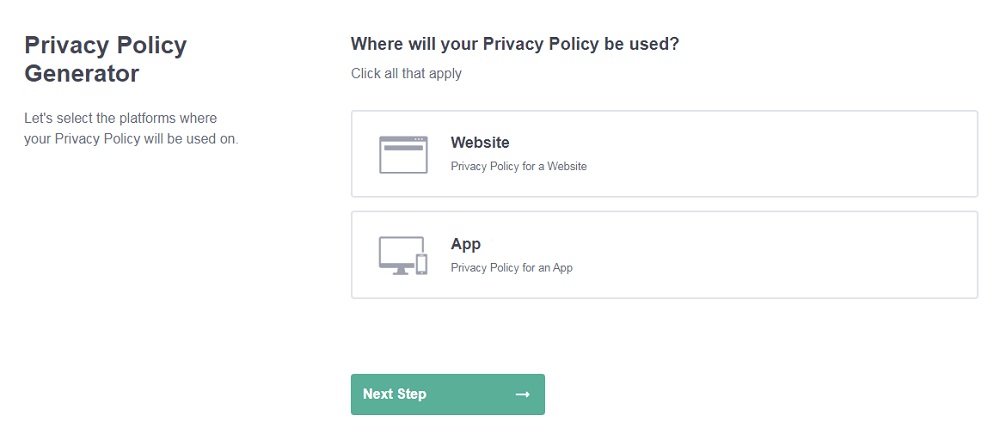
- Select the platforms where your Privacy Policy will be used and go to the next step.
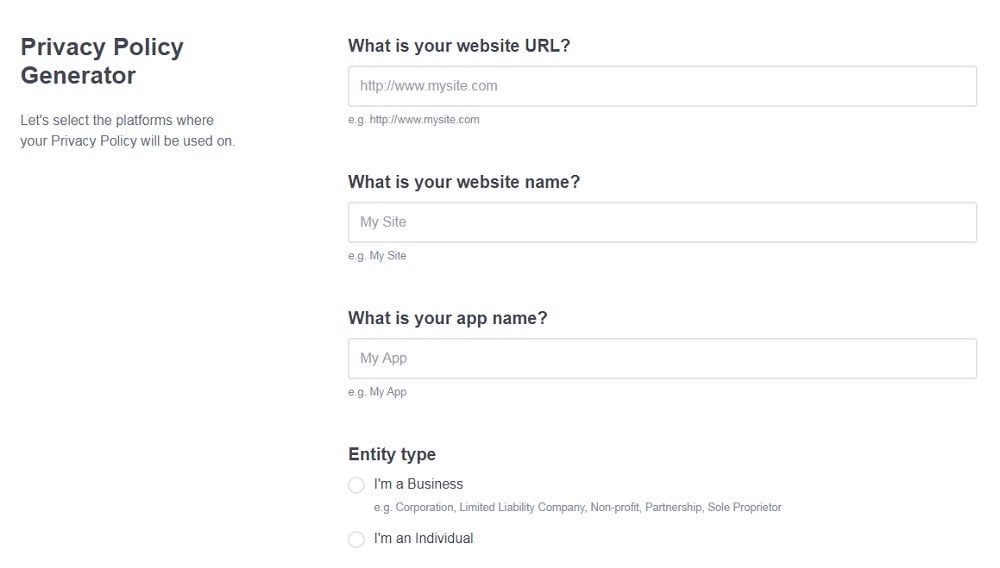
- Add information about your business: your website and/or app.
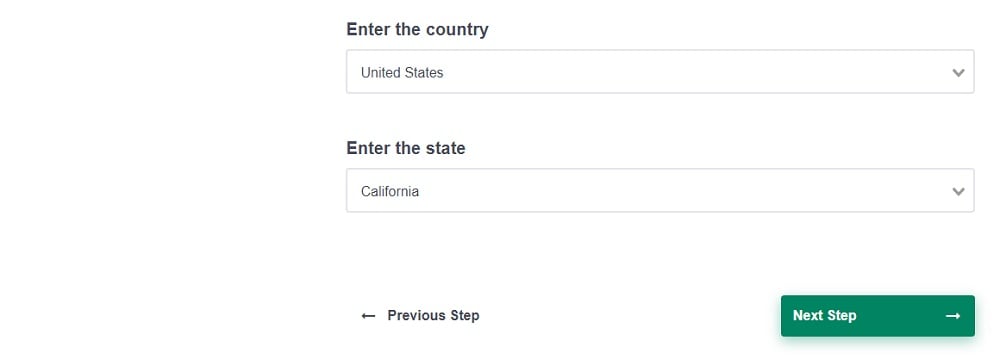
- Select the country:
- Answer the questions from our wizard relating to what type of information you collect from your users.
-
Enter your email address where you'd like your Privacy Policy sent and click "Generate".
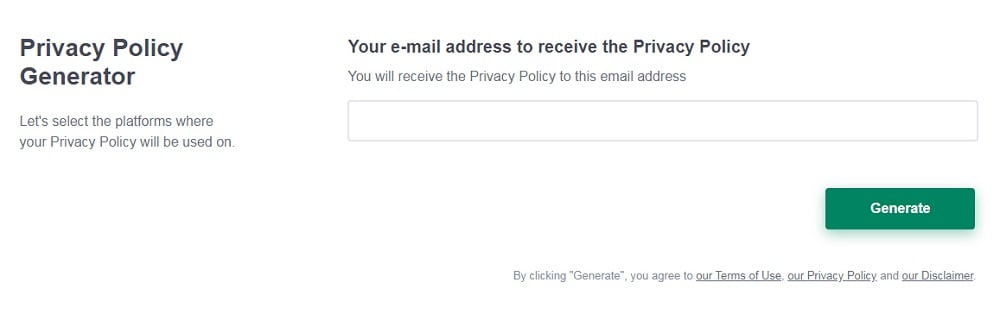
And you're done! Now you can copy or link to your hosted Privacy Policy.
- 1. What Constitutes Personal Data
- 2. Definition of a Personal Data Breach
- 2.1. How Data Breaches Happen
- 3. Challenges for Compliance
- 3.1. Endpoint Growth
- 3.2. The Cloud
- 3.3. Email: Ransomware, Malware, and Phishing Scams
- 3.4. Skills Gap
- 3.5. Insufficient Guidance
- 4. The Major Steps to Ensuring Data Breach Prevention
- 4.1. Risk Assessment
- 4.2. Intrusion Detection and Network Monitoring
- 4.3. Employee Training
- 4.4. Protection and Encryption
- 4.5. Network Security Policy
- 4.6. Transfer and Storage Protection
- 5. Recognizing a Data Breach: Steps to Take
- 6. Penalties for Non-Compliance
- 7. Conclusion
What Constitutes Personal Data
All the laws mentioned above have their own definitions of personal data, but luckily, they're very similar. The GDPR sets out the clearest, most comprehensive definition. According to Art. 4 of the GDPR, "personal data" is any information that can be used to identify a natural person, i.e., an individual or their household.
There's no exhaustive list of what constitutes personal data, but section 1798.140 of the CCPA sets out a few examples, including:
- Name
- Postal address
- Passport number
- Biometric data
- Employment data
What this means is that most businesses, whether you're a retailer or a construction company, handle personal data and must understand how to keep it safe from data breaches.
So, what exactly is a data breach?
Definition of a Personal Data Breach

The definition of a personal data breach is clearly defined in global privacy laws. Art. 4 section 12 of the GDPR defines a personal data breach as the unauthorized or unlawful alteration, destruction, or access to personal information.
What's important is that the breach doesn't have to be deliberate - it's still a breach even if it's accidental.
Essentially, it's a data breach when personal information is viewed or shared without permission.
How Data Breaches Happen
Data breaches occur for many reasons. It's not always down to hackers or cyber criminals. Here are some of the most common ways that data breaches happen:
- Employee accidentally reads a file they shouldn't have access to
- An employee deliberately accesses and changes information without authorization
- An unencrypted or unprotected device, such as a mobile phone or a laptop, goes missing
- Someone steals an unprotected mobile device
- Cyber criminals infiltrate your system through, for example, phishing emails or a direct network attack
In other words, it's easy for data breaches to happen, which is why it's so important you do everything possible to protect data under your control.
You'll notice that information doesn't have to be shared or leaked to still be considered "breached". For example, if an employee alters personal data held in a file, but they don't share the file with anyone else, it's still a breach. The whole point is that someone tampered with the data, or even just accessed it, without proper authorization.
So, how do businesses keep up with their data privacy compliance requirements, and what steps can you take to minimize the risk of a data breach? Let's take a closer look.
Challenges for Compliance

Every company faces similar challenges when it comes to preventing data breaches. Whatever sector you operate in, here's an overview of the most common challenges you may face.
Endpoint Growth
The increase in the number of devices that are connected to a single network, such as laptops, mobiles, and tablets, makes it harder for companies to adequately protect them all.
Now, companies need security solutions that can be easily scaled up to cover a growing infrastructure. For many businesses, however, their IT budget doesn't stretch to adequately protecting multiple devices. This can create risks.
The Cloud
While increasingly popular, migrating your business to the cloud isn't always easy. It's not always clear how to properly protect data transferred to and shared around cloud environments, and for many companies, security is therefore a major roadblock to going virtual.
Email: Ransomware, Malware, and Phishing Scams
Email-related data security breaches are on the rise, according to recent studies. Hackers and cyber criminals can easily send harmful software and codes over email to unsuspecting businesses. When an employee opens a harmful attachment, the computer is infected, and hackers can steal or corrupt sensitive information.
These are common areas and methods for data breaches.
Skills Gap
For some businesses, it's hard to find IT professionals with the right skillset to protect their company's cybersecurity. Why? Because hackers evolve quickly. Cyber threats are changing at such a rapid pace that many IT specialists simply don't have the knowledge to adequately protect companies from data breaches.
Insufficient Guidance
Although there are many data privacy laws around the world, the laws can't keep pace with this ever-evolving threat landscape. What does this mean for you? Well, what it could mean is that although you're technically complying with the law, you're not actually taking sufficient steps to protect personal data from unauthorized access.
The Major Steps to Ensuring Data Breach Prevention

If you plan on preventing a data breach, follow these steps:
- Adequately protect your infrastructure and the personal data you possess or handle
- Know how to safely dispose of data you no longer have the authority to hold
- Ensure you know how to recognize a data breach
- Set up clear procedures for staff to escalate any concerns
- Prepare a response plan for dealing with the breach
Be aware that this is not an exhaustive list (since, for example, some sectors have more specific requirements) but it's a very good place to start. Remember, though, that you only need to adopt safeguards that are proportionate for your organization.
For example, implementing large-scale, expensive security measures that cost $30,000 to run is disproportionate if it would only cost you $10,000 to fix a data breach. In this case, you're looking for a solution that costs less than $10,000 to implement, because then, the benefits outweigh the costs.
Risk Assessment
You must take steps to mitigate your cybersecurity risk, which typically means performing a proper risk assessment. When assessing your cybersecurity risk, consider factors such as:
- How data moves around your organization
- The size of your infrastructure
- How you store and archive data
- What cybersecurity procedures you already have in place; for example, encryption
- What you do with data you're no longer entitled to store
- The sufficiency of the cybersecurity policies adopted by your third party vendors
Tip: Knowing the key risks affecting your organization is central to reducing your security vulnerabilities.
Intrusion Detection and Network Monitoring
A reliable way to prevent data breaches is to detect possible threats, such as malware and phishing scams, before they infiltrate your system. You can think of intrusion detection like network monitoring. You're monitoring your infrastructure 24/7 to keep it safe from external threats.
There are many tools you can use, including:
- Remote surveillance
- Firewalls
- Antivirus software, which, like firewalls, are highly effective and often relatively cheap to implement
- Penetration testing and audits
- Software-based detection tools
Employee Training
Your employees regularly come into contact with personal data, which means you must train them on data protection good practices. Help employees understand the threats facing your business by:
- Offering regular training on how to spot data breaches
- Enforcing good practices including password protection
- Limiting how many employees have access to sensitive data
- Setting out clear procedures for raising security concerns
- Appoint a team to handle data security issues
Protection and Encryption
You aren't taking reasonable and proportionate steps to protect data from breaches if you don't keep a close eye on:
- How data's moving through your company
- How protected the data is at each step of its journey through the front and back ends of your infrastructure
Put simply, you're responsible for protecting personal data for however long it's in your possession, and at every stage, including disposal. Adequate ways to protect personal data from breaches include:
- Using encryption to "scramble" files and keep them safe during storage and transfer
- Using password protection
- Physically locking hardcopy documents away somewhere safe
- Erasing data securely by using special software
Network Security Policy
Policies such as a Network Security Policy demonstrate your commitment to keeping personal data safe.
A Network Security Policy allows you to:
- Identify the risks affecting your network
- Assess how you'll manage these risks
- Prove that your network can sufficiently safeguard personal data from a breach
At minimum, you need to include security clauses in your Privacy Policy.
Transfer and Storage Protection
Since data must be adequately protected at every stage of its journey through your infrastructure, you should employ adequate transfer and storage safeguards.
Examples of appropriate, cost-effective steps you can take include:
- Using wi-fi protected access (WPA) to password-protect your wifi network, and protect data moving across it
- Using a virtual private network (VPN) to enhance data security by encrypting your network itself
- Using secure sockets layer certificates (SSL) where possible
Recognizing a Data Breach: Steps to Take

If a data breach happens, the processes you put in place must enable you to do two things:
- Act quickly to mitigate the damage, and
- Inform affected individuals about what has happened
In terms of notification, you should set out your procedures clearly in your Privacy Policy. Let customers know how you plan on advising them on potential data breaches, and what steps you'll take to remedy the breach.
Here's an example from Barnes & Noble. You'll note that the company stresses there's only so much it can do to protect personal data. It can't guarantee to keep it safe at all times.
This is a good approach to take because it limits your liability while maintaining your compliance:
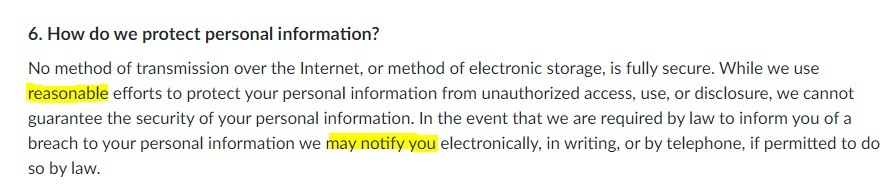
No matter how careful you are, breaches can and do happen. What matters is that you can show you took reasonable and proportionate steps to reduce the risk in the first place.
You should review your data protection strategies at regular intervals, especially if you're a growing business with expanding infrastructure.
Penalties for Non-Compliance
There are various penalties for non-compliance with data privacy laws. Very briefly, the severity of the penalty applies depends on many factors, including:
- Which law/s apply
- The scale of the breach
- Whether you took reasonable steps to reduce your cybersecurity risk
Penalties vary widely. Typically, you can expect to incur a financial penalty or a fine. If you face a fine, the GDPR, for example, sets out that it should be:
- Proportionate to the scale of the breach
- Enough to dissuade others from negligent behavior
Other privacy laws follow similar guidelines. In other words, financial penalties can be severe.
Conclusion
If you're responsible for any personal data belonging to an employee, customer, or other individual, you must protect it from unauthorized access. You only need to take steps that are reasonable and proportionate for your business, and you shouldn't warrant that data is safe at all times.
Breaches can and do happen, and limiting your liability is important.
To keep personal data safe, you should:
- Perform regular audits and risk assessments
- Use penetration testing to test the efficiency and reliability of your cybersecurity, by simulating false attacks
- Appoint a dedicated team, or individual, to oversee cybersecurity
- Train your staff on IT and cybersecurity best practices
- Set out clear procedures for identifying breaches, responding to them, and notifying affected individuals


